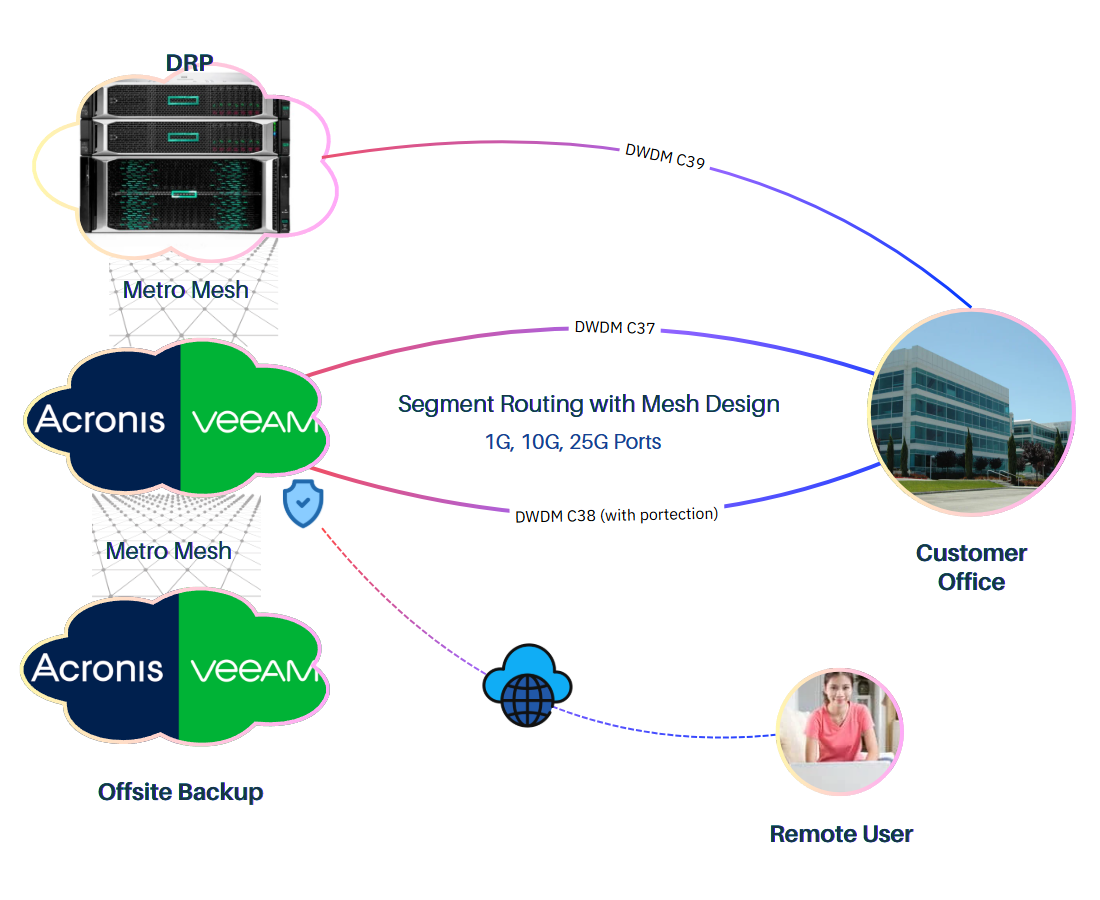
Offsite Backup
Never lose a file again; quickly move your data to new drives and computers.
Full image backups
Create complete system disk or partition replicas for efficient recovery of entire systems, individual files or folders as needed.
Backup and Transfer
Never lose a file again; quickly move your data to new drives and computers.
Realtime disk cloning
Create a disk clone on Windows or macOS without interruption, enabling seamless data migration to larger or faster disks, including the operating system, files, applications and settings.
Recovery drive
Effortlessly restore systems to identical or different hardware using bootable media and the integrated Survival Kit tool.
Microsoft 365 backup
Establish direct cloud-to-cloud backups for Microsoft 365 accounts, protecting emails, attachments and OneDrive files and folders.
Selective file and folder backups
Control the nature of your backups. Select individual files and folders that you want specific replicas of when you don't want a full image copy.
File synchronization and sharing
Replicate your local backup in the cloud automatically so you always have an off-site copy available for recovery. Following the 3-2-1 backup rule has never been easier.
Dual Protection
Create multiple copies of your data locally and in the cloud, ensuring adherence to the 3-2-1 backup rule and the availability of off-site copies for recovery in case of a loss of a local backup.
Cloud restore
Access files in your cloud backup from anywhere: download a single file or folder to recover it to another machine, or access your data from another device while traveling.
User-specified encryption keys
Establish encrypted backups for individual users in your family, secured by their passwords.
End-to-end cryptography
Enterprise-grade AES-256 encryption protects backups on-site, in transit, and in the cloud, maintaining data privacy for everybody, including Acronis.
Secure data storage infrastructure
Backup data to Acronis data centers, which adhere to stringent security standards, including on-site protections, 24/7 video surveillance, and biometric access control.
Try and Decide tool
Safely test new software, drivers, system updates and settings with the option to revert to the previous configuration.
Cybersecurity
Prevent viruses and ransomware, and never lose time to recover your system again.
Anti-ransomware and cryptojacking protection
Defend files, applications and systems against ransomware and cryptojacking attacks through advanced detection and prevention technology, enabling automatic recovery of impacted files.
Two-factor authentication (2FA)
Protect your account by requiring two different forms of identification, such as a password and a unique verification code.
Vulnerability assessments
Evaluate potential security weaknesses in the operating system and applications with a comprehensive vulnerability assessment tool, offering recommendations for updates to enhance security.
Real-time protection
Safeguard devices and backup files against malicious activity, using continuous threat monitoring to address previously unknown risks.
Malicious URL filtering
Restrict access to URLs attempting to deliver malware, ransomware or cryptojackers to systems.
On-demand antivirus scan
Execute malware scans as needed, selecting between rapid file scans or comprehensive system analyses.
Signature-based threat analysis
The threat database is updated every five minutes, ensuring continuous defense against emerging risks.
Behavioral analysis engine
Detect malware upon execution using a dynamic detection engine that identifies threats based on interactions with the system.
Quarantine and exclusion management
Isolate potential threats while maintaining approved program functionality through controlled exclusion lists.
Videoconference security
Protect privacy during Zoom, Cisco Webex or Microsoft Teams videoconferencing sessions.